Introduction
Offensive security testing is only a single facet of a complex system for improving an organization’s overall cybersecurity and resilience against threat actors. However, with a multitude of different options for testing and exercises, it can often be difficult to determine when and what to use for improvement.
A deep understanding of your organization’s security maturity is one important factor for this decision, but the thought process behind why and how to use certain types of tests or exercises bears even greater importance. Cognizance of these factors will improve the efficacy of offensive testing and exercises, and help to formulate a structured, cyclical plan. The result is an immense boost to an organization’s readiness when faced with a real-life threat.
The goal of this article is to enable a paradigm shift in the way organizations think about this decision-making process, and to dispel complexities by proposing a structured approach when creating a security improvement plan using offensive testing.
Self-awareness
Improving cybersecurity is analogous to a properly structured workout regimen. When first starting, it’s important to understand initial limitations and to operate within realistic capabilities. When starting to incorporate weight training into a training regimen, it’s unlikely that it will be possible to lift an immense amount of weight with no prior training. There is a risk of performing the exercise incorrectly, which can cause injury and severely impede further progress and growth. Similarly, if an organization has not incorporated offensive testing into their security plan before, regardless of their assumptions about how solid their security may already be, it is best to start slowly and gradually level up. Failure to do this can limit the benefit and efficacy of a test or exercise, which is something every organization should want to avoid to maximize return on investment of these services.
Posture and a Firm Foundation
Building a solid security foundation is paramount when it comes to offensive exercises. Having an ideal security posture comes from an intimate knowledge of your organization’s assets, as well as ensuring it has a minimal attack surface through the reduction of vulnerabilities. These are both important first steps towards maturity. Without these foundational steps, the security structure can easily collapse when introducing live threat actors into the environment.
To continue the weight training analogy, when learning how to correctly perform an exercise, such as a deadlift, perfect posture is key when aiming to lift heavier weight. While issues may not be apparent earlier on when lifting lighter weights, failure to implement correct posture and form will be detrimental later, when adding more weight and stress. The same is far truer for security as the complexity of environments and networks grows.
It’s recommended to begin by utilizing vulnerability assessments to take inventory of assets and to identify and remediate easily exploitable low-hanging fruit. Next, penetration testing (pentesting) from different angles, such as external, internal, wireless, and application testing, can identify deeper issues and misconfigurations present within the environment. Issues like gaps in detection, weak passwords, and poor security practices when remediated creates a firm foundational security posture ready for more advanced exercises.
Applicable Tests:
- Vulnerability Assessments
- External Pentests
- Internal Pentests
- Wireless Pentests
- Web Application Tests
How Secureworks Can Help
The Secureworks Adversary Group offers a wide variety of offensive testing services to accommodate our customers’ needs. This ranges from traditional services such as pentesting and application security to highly specialized and custom engagements for autonomous vehicles, lost laptop, hardware, physical, and more.
Full details of all service offerings provided by the Secureworks Adversary Group can be found here.
Developing Strength
After remediating based on lessons learned from previous test to establish a strong structural foundation where there is a deep understanding of assets and all low-hanging fruit has been removed, the next step is to examine and test assumptions for detection, prevention, and response capabilities.
While vulnerability assessments are primarily focused on the discovery of vulnerabilities and misconfigurations, and pentests are noisy by nature without paying heed to stealth and advanced operational security factors, both can still contribute to painting a good picture of how well security devices such as EDRs and network-based intrusion detection systems alert to common activity. With this said, however, it is important to dig even deeper by applying a different strategy to look at elements that are not always apparent during traditional pentesting.
When starting endeavors to improve detection, prevention, and response capabilities, it is recommended to begin by first examining common tactics, techniques, and procedures that are used in the wild by known threat actors to ensure protection against what can be a large percentage of potential attacks. Leveraging opportunities to run through scenarios conducted by the Red Team gives the Blue Team a chance to learn about techniques and gain deeper insight about how they are used and what they look like from a telemetric standpoint in a safe environment, but also practice and gain game-time experience. This data can then be used to identify gaps in security controls and detections, which can be harnessed for detection creation and tuning to close visibility gaps and harden defenses even further.
Applicable Exercises:
- Collaborative exercises between the Red Team and Blue Team
- Emulation exercises
How Secureworks Can Help
Secureworks Adversary Group offers several exercises under the Adversary Exercises service line that provide a collaborative approach to offensive testing via the use of various playbook scenarios, as well as a full scope threat intelligence-based emulation that explores known threat actors’ tactics, techniques, and procedures.
Learn more about Secureworks Collaborative Adversary Exercise and Adversary Emulation Exercise
Leaving Comfort Zones
The threat landscape is continuously evolving with newer techniques and derivatives of techniques which aim to bypass detections. It is not enough to build detections or hunting playbooks around tools themselves.I Instead it’s critical to deeply understand the underlying primitives of the tools and techniques. Becoming comfortable with exercises and operational flows for detecting and responding to activity demonstrates progress and higher security maturity.This is exactly the correct time to make modifications so that the Blue Team is challenged and pushed even further to progress.
To use the workout regimen analogy, one of the best ways to ensure constant progress and to break through plateaus is to mix up routines to stress muscles in different ways — to keep the body guessing. This principle applies to the Blue Team as well. While performing exercises that aim to emulate adversaries and the TTPs they adopt is a solid path to enhancing security, this only explores ”known bads” and what has been seen and attributed to identified adversaries. Frequently challenging assumptions about security controls and what the team can respond to is critical for ensuring that organizations are prepared for any kind of threat, and this can be achieved by including “unknown bads” in the exercise cycle.
If your organization has implemented new detection and prevention capabilities that take attack primitives into consideration, or are exploring how to examine this aspect, leveraging a Red Team with heavily customized TTPs (or even different threat models) to stress test the Blue Team and test assumptions about the present state of defenses is the perfect next step.
Applicable Exercises:
- Simulation exercises
How Secureworks Can Help
As an advanced offering for more mature organizations, within the Adversary Exercises service line, Secureworks Adversary Group also offers a full scope simulation exercise that leverages customized tactics, techniques, and procedures to push the Blue Team out of their comfort zone.
Full details of the exercise can be found via the following link: Adversary Simulation Exercise
Conclusion: Stay Sharp with a Cycle
As technology, assets, and environments continue to change over time, organizations need to remain up to date with the latest trends. Linear progression towards more advanced exercises such as the adversary simulation exercise demonstrates increased security maturity, but these exercises are all point-in-time. As such, sticking with the same type of exercise after reaching a certain level of maturity should be avoided. This means that creating a proper cycle of each exercise is the best way of maintaining the best security posture possible.
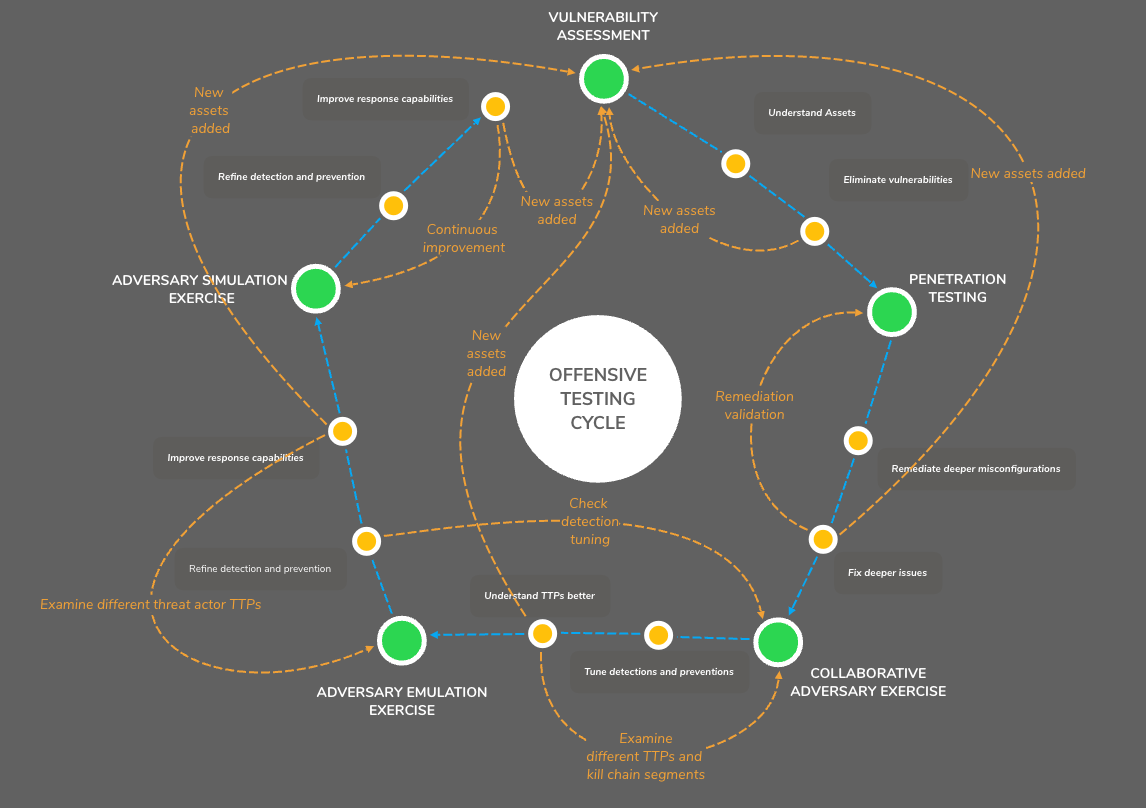
The following mind map illustrates an example of how each of the above exercises can be positioned in a cycle for security improvement. The blue dotted line represents the progression of maturity through the different types of assessments and exercises and the orange dotted line represents cyclical movement for improvement at various junctures when there are changes in the environment or a necessity for circling back around to a specific exercise.
It is important to note that progress — and the cycle itself — can take on different shapes depending on the organization and environment, and this should be dictated by self-awareness and being honest about where your organization is positioned in the maturity spectrum.
By taking all the above into consideration and adopting a holistic view of security improvement, these factors should drive the decision-making process for how to effectively spend security budget to maximize return on investment for continuous security maturity growth and ever-increasing resiliency against any threats that may come along. Learn more about the role adversarial security testing plays to strengthen your security awareness and test dangerous assumptions that may be putting your organization at risk. As the adage goes: the best defense is a good offense.
Secureworks Adversary Group Can Help!
Building a security program that properly incorporates offensive testing may seem daunting at first, but Secureworks® Adversary Group is here to help. Our consultants are available to discuss options to find the best services to meet your needs and can help organize a solid cycle to get you on track for security improvements. Get started on your security enhancement journey or continue momentum with your progress by directing inquiries here.

.png?h=310&iar=0&w=420&hash=0B9488A86028BA379F679DEDB451DABC?io=transform:fit,width:642,height:330)